Consumer preference services are a proven tool to curb the invasive use of personal data through cold calling and cold mailing. They protect the integrity of the marketing industries that rely upon telephone and post. However, they fail to address the root cause of customer abuse—data gathering, CRM, and analytical processes that systematically abuse customers without their knowledge.
This article explores the case for an identity preference service to protect the integrity of the entire relationship marketing industry.
In the UK, the Telephone Preference Service (TPS) and Mailing Preference Service (MPS) are industry initiatives designed to protect the effectiveness of an existing outbound marketing practice—telesales and direct marketing—which are hateful to many people because of personal privacy invasion, time-wasting, and wastefulness of natural resources.
Similar registers (e.g., Do Not Call in the US) exist around the world. While MPS is purely self-policed by the Direct Marketing Association, TPS has regulatory force under the 1999 Telecommunications regulations and is an organisation in its own right. TPS is much more actively promoted.
The two schemes act to restrict the access of interlopers into these trusted channels, but allow existing relationships to continue a customer "conversation" unheeded. The following chart hints at the prevailing levels of irritation with out-of-relationship contact and reinforces the minimal perceived benefits.
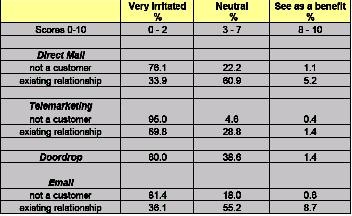
Source:CACI
By focusing social responsibility within the industry, TPS and MPS have helped defuse and divert antagonism away from specific marketing firms and media owners (Royal Mail & BT) by moving well ahead of strict legal requirements.
As aggregators and conveyors of individual preferences, the schemes protect the trusted reputation of a medium (telephone and post) and thus maintain the effectiveness of those communications channels for those who use them responsibly.
TPS and MPS work as a voluntary mechanism through which users register their desire not to receive invasive sales calls, and reputable companies abide by these recommendations, removing them from any call lists—and facing regulatory censure for any noncompliance.
From Industry Initiative to Competitive Platform
The growing success of telephone preference services, despite historically moderate publicity, has encouraged media owners to sit up and take notice.
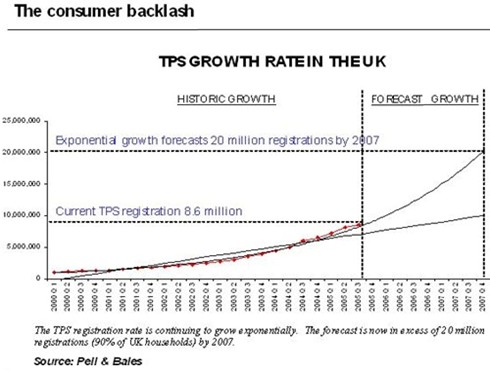
The rapid escalation of interest and registration in TPS in particular has prompted BT (as the initiator and key stakeholder in TPS) to take defensive action, however, as its own B2C marketing efforts are undermined by TPS.
It has thus created BT Privacy, effectively a bundled service which incorporates TPS and caller identification, but also prompts users on registration to exempt BT alone from these TPS restrictions. BT Privacy also promotes value-added paid-for services such as call barring and withheld-number blocking services thorough this medium, as well as selling discounted phones with caller ID facilities.
The Rationale for IPS
These core issues of privacy invasion, personal time wasting and resource waste through unauthorized data processing and data verification apply equally to the "upstream" field of personal data management as they do "downstream" in organizing mailings and telephone calls. If anything, the problem is worse, as the legislation (e.g. Data Protection Act) is weak and regulators (the Information Commissioner) disempowered and under-resourced.
The real difference here is that the life-intrusion in this remote personal information management is invisible, virtual, and insidious. Unlike a phone call or a piece of direct mail, personal information "system abusers" or are invisible to the individual.
The risks of this lack of "data subject" accountability include the denial of access to legitimate social entitlement to personally appropriate services (credit, benefits, healthcare, mobility)—at a fair and justifiable rate.
Other impacts include the leaking of personal data to criminal gangs and the perpetration of ID fraud by insiders or outsourced data managers at companies that the individual may have no conscious relationship with. The super-fueling of a deluge of unwanted and undesired and inappropriate mailings, spam emails, and telephone call is a relatively minor but still disruptive consequence.
Instead of protecting a promotional marketing function, however, IPS works to protect the reputation and integrity of the internal data management function—the CRM team. CRM systems breach privacy, waste individuals' time, and squander resources. The "medium" to be protected with IPS is the invisible personal data-mining based on uninformed consent or reluctant compliance, which underpins all personal data management. IPS is the savior of CRM.
The Role of IPS for the Individual
At present, the vagueness of opt-ins and prevalence of data reselling effectively compromise the ability of individuals to control their personal data chain—the very data chain that drives the quality and integrity of their relationships.
Similarly to MPS and TPS, most individuals will wish to share personal their "identity" richly with existing service and product suppliers, and IPS registrants will wish to restrict the data access and processing of those with whom they do not have relationships and do not wish to have relationships.
IPS gives individuals the opportunity to set unilateral rules over their identity management preferences, which all data users must abide by. These clearly stated preferences take precedence over other implied consents. The purpose of IPS is (1) to protect consumers from the invisible risks and unforeseen consequences of unintended data opt-in and the remote and unaccountable trafficking of their identity, and (2) to ensure the accountability of their identity as held by organizations with which they do wish to interact.
A Social Revolution
Just as TPS has successfully merged a key social responsibility benefit with broader marketing objectives for BT, so data processors, storers, and aggregators stand to gain enormously from IPS by proactively offering individuals self-protection and personal information management solutions in addition to brokering IPS registration.
This "preference service" model of voluntary registration offers an opportunity to turn social responsibility into social advocacy, increasing the potential of the individual to maximize the return on their personal assets (time, energy, attention, money) and ultimately, identity—that complex fusion of who we are and what we are—not just as individuals but also as social citizens.
At present, the use of personal data performs an undeniable socioeconomic function: to accurately allocate collective resources to those individuals who are most "deserving" in the minds of the resource controllers. Personal information enables the individualization of value:
- For corporations: Personal data enables resources to be allocated to the most profitable customers at lowest risk of waste—through default or over-investment.
- For government: Personal data enables resources to be directed to the most "deserving" citizens at lowest risk of waste—through fraud or over-dependency.
To this common and distinctly actuarial end, government and corporations use personal information to track behavior, biography, and biology in order to optimize their resource matching and improve their risk assessment.
Clearly, these adjudications of human "worth" or investment "merit" depend on the prevailing value-metrics, values-judgments, and time horizons of the institutions concerned. Those rule-based decisions have unforeseen, and (without IPS) uncontrollable, social consequences. Critically, they are unaccountable to the individual concerned.
This problem is severe enough when the issue is creditworthiness or insurance-worthiness. But when the resource concerned is education, or healthcare, or freedom, assessments of "deservingness" take on a much more sinister nature.
The fact is, that even if the personal data held is correct and consistent, the prevailing top-down, CRM-based model carries many risks for the individual—loss of control, the indignity or depersonalization of its gathering, the inconvenience of its monitoring and validation, and, most critically, the implicit persistence of all historic social status and personal deeds.
Finally, the trafficking of our information creates the ability to generate derived knowledge—for example, a map of our total indebtedness or past allegiances—and make those available to third parties without our explicit consent or knowledge.
We are, through ubiquitous information, trapped by own biography, not just our own biology. Thus all citizens, from bankrupts to teenage drug takers, find it impossible to reinvent themselves. Personal information creates a permanent underclass. Our personal history is compelled to repeat itself. The first time as tragedy, the second time as farce, the third time as soap opera.



